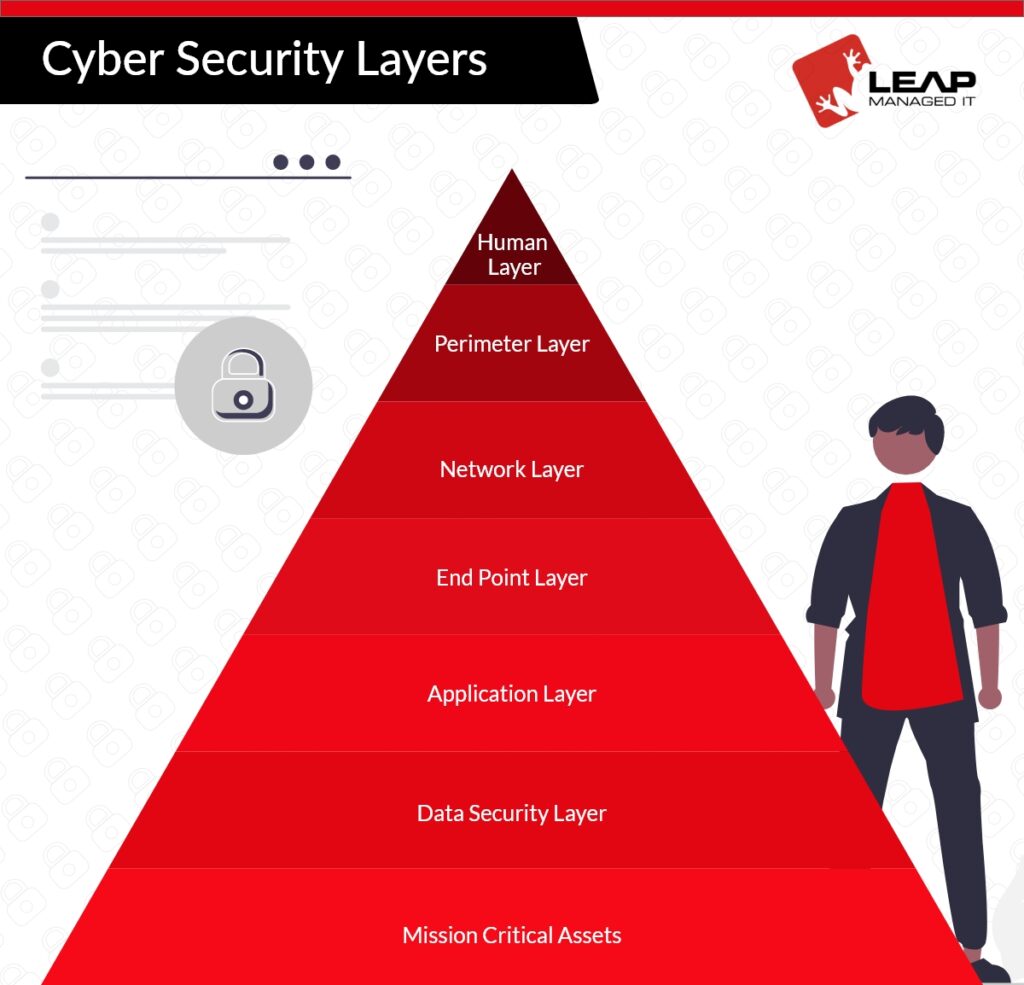
A Master IT plan is a concept of understanding the current system, defining the strategies, and developing a road map to the targeted achievement. Defining an organization’s strategic target is an efficient way to achieve its goals.
In this article, we will learn how Leap Managed IT can offer Ridiculously Helpful Managed IT support for the well-being of a business.
Leap’s Managed IT Services
Imagine John Doe handles everything under the security desk of your organization. He is the one who fixes when everything goes wrong, protects all your systems. Don’t you think this would be quite a hassle and even items can fall through cracks if John is managing it single-handedly?
This is the situation evolving in most organizations. A single person managing everything will leave your organization vulnerable to security breaches and other system problems. This is where the option of outsourcing a managed IT service provider comes into the picture. Leap Managed IT is a one-stop solution for all IT services as their team offers ridiculous support for your IT needs, allowing you to focus on your core business.
Every organization is different and everyone has their own frustrations, requirements, and goals. Leap’s IT services identify what is yours and design a plan addressing each of them. The team of experts from Leap understands your struggles, evaluates your system/policies, and comes up with an IT Master Plan and solution to help you in achieving your goals.

The Process at Leap Managed IT
An overview of Leap’s process of developing an IT Master Plan,
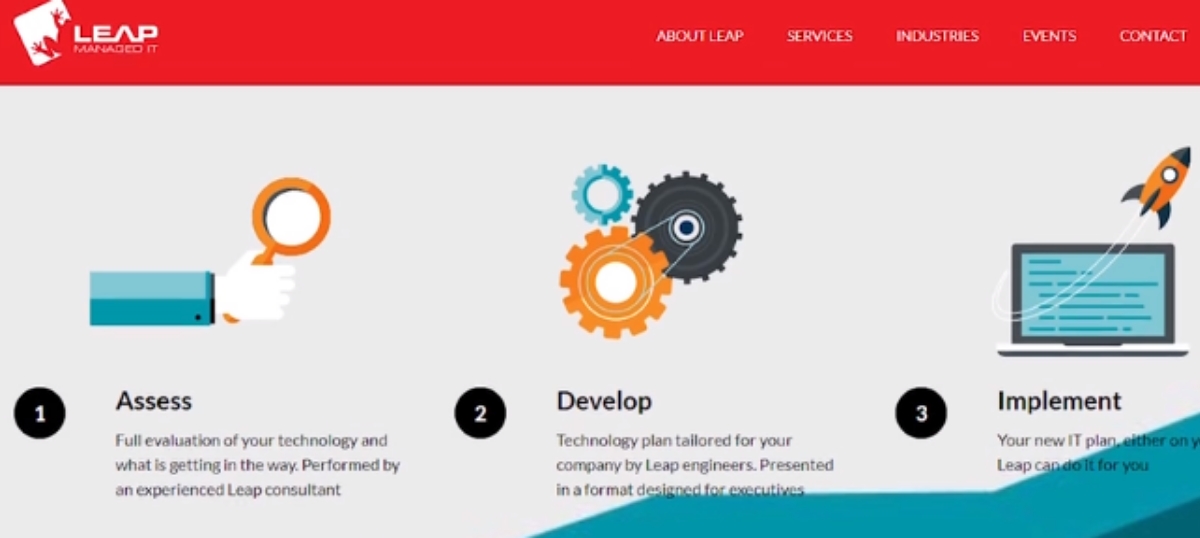
Assess:
- Schedule a consultation to understand your current IT status
- Perform complete IT audit and analyzes hardware, software, and infrastructure
- Conduct analysis and provide a report on your current IT status, including security threats, network problems, server problems, and other related issues
- Offer recommendations that will help improve your efficiency and operations
Develop:
- Create a roadmap addressing the challenges mentioned in the audit
- Create a technology environment to keep you in a controlled state, so that you will be focusing on your improvements and evaluation
Implement:
- Help to keep your technology and business ahead of the curve
- Either you can own the IT plan or Leap can implement it for you
- Schedule an initial review, 30 days after going live
- Monthly or quarterly reviews are scheduled to ensure that we are aligned your technology needs to that of your goals, strategy, and budget
Below is the workflow that Leap follows during the development of an IT Master Plan for a business.
Initial Consultation
At Leap, the team schedules an initial consultation with you and any other critical resource from your business. During the consultation, the team learns about the struggles and frustrations that your business is facing. Knowing and learning the root causes of the problem would help in coming up with an effective solution. In addition to this, the team also makes an effort to learn and understand your business goals to have a clear idea in developing a suitable plan for your business.
Onsite Evaluation
After the consultation session, the team takes it further to the evaluation of your IT infrastructure. Here, they will conduct an assessment of your network, devices, and security to identify any vulnerabilities. After the evaluation of the overall infrastructure, the team also reviews your compliance policies and business continuity plan. This would help the team to have a clear idea of what action needs to be implemented for the well-being of your business.
IT Master Plan Development
Once the analysis of security vulnerabilities, weaknesses, security risks, and business targets are completed, the team develops a customized IT blueprint tailoring your business needs. Furthermore, the Leap team will also come up with recommendations on hardware, software, and processes.
IT Master Plan Meeting and Implementation
Finally, the team calls up for a discussion on the vulnerabilities and solutions. Here, the aim of the discussion is to review the IT Master Plan developed and implementation for your business. You can either opt for Leap Managed IT to implement the plan, or Leap can just hand it off to you.
What Can You Expect From Leap Managed IT?
Your business can experience the below if you are hiring Leap Managed IT for managing your IT services,
- They thoroughly understand your business with the goal of learning
- Performs an in-depth analysis to understand your IT frustrations and identify any threats, concerns, and vulnerabilities
- Identify areas that require improved security measures
- The team takes care of the managed IT services completely, monitors and also addresses threats and changes if any
- Effective communication throughout the entire organization
Are you looking for expert guidance in developing an IT Master plan for your business? Services at Leap begin with an IT Master Plan. Our expert team at Leap Managed IT can help you identify the obstacles, create an IT blueprint, and grow your business.
Want to learn more about having a sustainable approach to IT? Speak with our Ridiculously
Helpful team to learn how we can create a comprehensive roadmap for your technology. This will help keep you on track while you focus on enhancing your business.
See how we help businesses in the Indianapolis area with all their managed IT needs. It all starts with our Master Plan. Click Here to watch, and we look forward to hearing from you.
Like us on Facebook and get more Ridiculously Helpful tips for your business.